
SFTP Authentication
Author: Conrad Chung, 2BrightSparks Pte. Ltd.
This article discusses the basics of what SFTP is and the various authenticating methods in which a user can use to connect to an SFTP server (depending on how the server is set up). In addition, we will be discussing how a connecting client can check to ensure the SFTP server is authentic.
To transfer files securely using SFTP, you will need to use a client that supports the Secure Shell (SSH) protocol, like the PC backup & synchronization program - SyncBackPro. Note that SyncBackFree and SyncBackSE do not support SFTP, and while SyncBackSE supports the FTPS protocol, it is unrelated to SFTP.
SSH in SFTP Servers is an encrypted network protocol that uses public key cryptography to create a more secure method to authenticate a client’s identity and rights to access a server.
In SSH, there are two sets of public/private key pairs (or four keys), which are:
- User (Client) Public Key
- User (Client) Private Key
- Host (Server) Public Key
- Host (Server) Private Key
Validation of the Server Public (Host) Key
A host key is the SFTP server’s public key. Ensuring the SFTP server is validated is an important aspect of the SFTP protocol. It is designed to protect against man-in-the-middle attacks where the hacker intercepts and relays an impersonated message to the other party. Host key validation ensures the FTP server that a client is connecting to is verified as the correct one. When the client connects to the server, the server’s public key is returned and the client may be prompted to accept the host key (if connecting for the first time). Once accepted, this key will be stored within the client, which will then be used to check if the Host key matches each time it connects to the SFTP server.
Note that host key validation is performed prior to any client authentication process starts, which only takes place if the server validation is successful, otherwise the connection will be aborted.
Important Note - the Host key (server’s public key) is different from the user’s public key. The former (host key) is used to validate the server’s identity by the client while the latter is used by a client to authenticate and login to an SFTP server.
When SyncBackPro connects to an SFTP server for the first time with host key validation enabled, you may be prompted with a message like this:
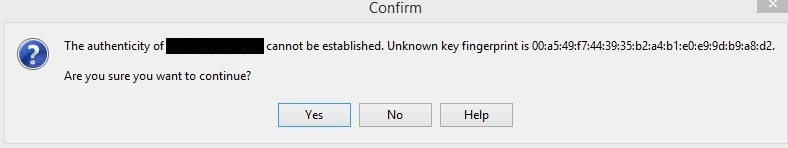
A hash fingerprint of the host key is displayed to the client. The user should use a secure method to verify the host key and ensure it matches the correct SFTP server. Once the server is verified and the host key is accepted, it is saved by the SFTP client so it can be used automatically in a future validation process whenever the client connects to the server. If the incoming host key does not match against the previously saved host key, the user may be prompted with the following message:
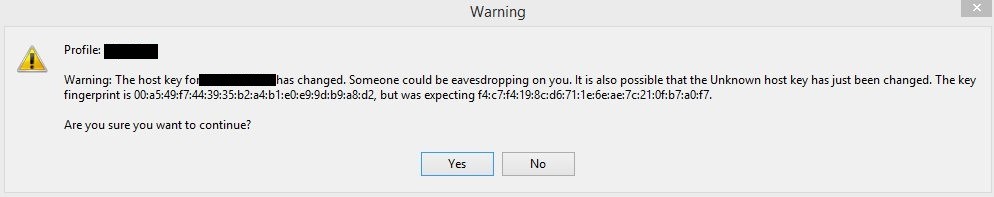
This message is to warn the client that the saved Host key does not match the incoming host key from the SFTP server. In the worst-case scenario, this message may imply that the server has been compromised or there is a man-in-the-middle attack. However, this is usually not the case. Some of the likely cause of this message may include:
- The user may have mistakenly loaded the user public key into the SFTP host key field, mistaking the user public key is the same as the server host (public) key
- The system administrator may have changed the host key, or he re-installed the server and used a new host key
- The user is using the wrong host key
The option to review or change the “SFTP Host Key” option is at:
Modify > Expert > FTP > Advanced
settings page of the SyncBackPro profile.
Client Authentication
There are several methods to configure the authentication procedure on an SFTP server. The three authentication methods supported by SyncBackPro are:
- username and password
- a username with a user’s public/private key
- a username with a user’s public/private key and password
Client Authentication using Password
This is the simplest form of authentication using the traditional username/password method. A client logs in to SFTP using Username/Password. No user private/public keys are required (although the client may still get prompted by the server to validate the host key). Note that some SFTP servers may be configured to disallow password authentication by default, which will result in the connection attempt to fail. The “username” and “password” can be configured under:
Modify > Expert > FTP
settings page of the SyncBackPro profile.
Client Authentication using Public/Private key
Public key authentication is a method where the SFTP client identifies itself to the server by using public/private key pairs. The client first generates a pair of public and private keys from his own computer using third party key generation tools like PuTTYgen, etc. Prior to connection, the user’s public key must first be uploaded and registered on the SFTP server. Then the client’s private key is loaded via the “SFTP Private Key” option of:
Modify > Expert > FTP
settings page of the SyncBackPro profile.
Before any client authentication takes place, the client may get prompted by the SFTP server to validate the host key when establishing connection with it. Once server validation is complete the client will encrypt a signature using the loaded private key and sends it to the server. The server then verifies this signature against the stored user public key. Once verification is successful, the SFTP will grant access to the connecting client.
Client Authentication using Public key/Private key and password
Do note that the password described in this section is not referring to the login password, but rather this is the password (or passphrase) for the private key. Public/Private key and password configuration is similar to steps described in the latter section, except that it includes the private key’s password.
When using public key authentication, you store the private key unprotected on your computer. As a result, if anybody gains access to this private key on your PC, they would be able to log in to your SFTP server using your account. One way to prevent this is to encrypt the private key with a password/passphrase. To use this key, the user must first decrypt it by entering the key’s password under the “SFTP Private Key Password” option, located at:
Modify > Expert > FTP
settings page of the SyncBackPro profile.
Without the password, the private key cannot be used by anybody else other than the original owner.
Secrets Manager
Introduced with SyncBackPro V11, a secrets manager can be used to retrieve your SFTP username, password and/or key instead of it being stored locally. A Secrets Manager (AWS Secrets Manager, Azure Key Vault, Google Cloud Secret Manager and HashiCorp Vault) is like a highly secure digital vault that helps you store and manage important secrets, such as passwords, encryption keys, and certificates. It's like having a special safe for your sensitive information in the cloud. A Secrets Manager ensures that your secrets are stored in a protected and encrypted environment, keeping them safe from unauthorized access. It also helps you control who has access to your secrets and allows you to easily retrieve and use them when needed. Just like a physical vault protects valuable items, it safeguards your digital secrets, providing peace of mind and making it easier to manage and secure your sensitive information in the cloud.
Conclusion
Besides providing encryption via a secure channel, SFTP provides a way to authenticate both the user and host. Hopefully, this article was helpful in understanding the basics of server validation and client authentication, as well as the configuration steps necessary to setup an SFTP connection.
Noted Customers
© 2003-2025 2BrightSparks Pte. Ltd. | Home | Support | Privacy | Terms | Affiliate Program


















