
Understanding OAuth2: Secure Authorization for Cloud Services
Author: Kostas Tsakiridis, 2BrightSparks Pte. Ltd.
With the advent of Internet and the development of various web application and services, such as email, it became necessary for users to share their valuable credentials with applications in order to be able to access their resources on websites and services. For example, an email application would require the user’s username and password in order to connect to the email server and retrieve/send emails.
It became evident that such practice is insecure similarly to giving your house keys to a stranger. Since the same credentials could be used for accessing the actual account information, serious implications would arise if those keys had been stolen or leaked.
In 2006, a new method of access delegation went into development, which was called OAuth (sort for “Open Authorization”), that would grant applications and services delegated access to users’ resources without the need to share their credentials and would provide access only to resource users wanted to access. For example, an email application can access only the user’s mailboxes and nothing else, or a file manager application can access the user’s files stored in cloud storage.
Eventually OAuth became an industry standard and currently its latest revision 2.0 is being used by every major company such as Amazon, Facebook, Google, Microsoft, Twitter and many others. Applications that need to access resources on behalf of the users have no other option but to use OAuth in order to be authorized to do so.
The current OAuth 2.0 is an improved version of the original OAuth 1.0. A newer version, OAuth 2.1 is in draft stage and consolidates changes made to OAuth 2.0 over the years since its introduction plus some security enhancements.
How does it work?
The OAuth is essentially a workflow protocol describing the steps taken leading to a successful authorization. In brief, its purpose is to guide the user to a trusted authorization server, let the user authenticate and provide consent, and in return grant permission to the application to access specific resources with the issue of a unique token.
This flow happens in the presence of the user, with the user participating in various steps of the flow, making him fully aware of the process.
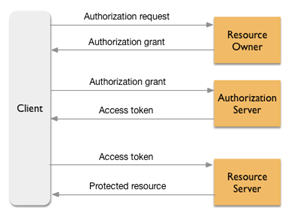
- The user (via the application, e.g. SyncBackPro) sends an authorization request to the authorization server responsible for the user’s resource, usually via a web browser session. For example, if the user wants to access files stored on Microsoft OneDrive, the request will be sent to a dedicated Microsoft webserver using a predefined set of parameters which identify the type of request and the ID of the application. Note that no private credentials are being sent with this request.
- Upon receipt of the above request from the server, a web page will request the user to identify, and once this is successful, the authorization server will display an authorization code to the user. This code will be either entered manually into the waiting application (usually with a copy-paste action) or it may be read automatically by the waiting application.
- The application will next create a new request using the above code it received, and send it back to the server, in order to exchange it with an access token. The server will verify the contents of the request and if it finds everything in order it will send back the access token to the application.
- The application stores the access token locally and uses it for any necessary tasks it may perform in the future. As long as this token is valid (each website/service has its own rules to determine validity) the application can use this token in every request it sends to the server and access the user’s resources.
All the above requests to the servers are done by using Hypertext Transfer Protocol Secure (HTTPS) which is exactly the same method used when browsing a secure web site, thus making it safe and easy to implement.
Does SyncBack use OAuth?
Yes, SyncBack implements OAuth 2.0 when authorizing connections to various supported cloud storages and services such as OneDrive, Google Drive, Dropbox, Office 365, etc., making it easier for users to create multiple profiles targeting the authorized cloud accounts.
Noted Customers
© 2003-2026 2BrightSparks Pte. Ltd. | Home | Support | Privacy | Terms | Affiliate Program















